Correcting wrong info reinforces false beliefs
From Jonathan M. Gitlin’s “Does ideology trump facts? Studies say it often does” (Ars Technica: 24 September 2008):
We like to think that people will be well informed before making important decisions, such as who to vote for, but the truth is that’s not always the case. Being uninformed is one thing, but having a population that’s actively misinformed presents problems when it comes to participating in the national debate, or the democratic process. If the findings of some political scientists are right, attempting to correct misinformation might do nothing more than reinforce the false belief.
This sort of misinformation isn’t hypothetical; in 2003 a study found that viewers of Fox News were significantly more misinformed about the Iraq war, with far greater percentages of viewers erroneously believing that Iraq possessed WMDs or that there was a credible link between the 9/11 attack and Saddam Hussein than those who got their news from other outlets like NPR and PBS. This has led to the rise of websites like FactCheck and SourceWatch.
Saying that correcting misinformation does little more than reinforce a false belief is a pretty controversial proposal, but the claim is based on a number of studies that examine the effect of political or ideological bias on fact correction. In the studies, volunteers were shown news items or political adverts that contained misinformation, followed by a correction. For example, a study by John Bullock of Yale showed volunteers a political ad created by NARAL that linked Justice John Roberts to a violent anti-abortion group, followed by news that the ad had been withdrawn. Interestingly, Democratic participants had a worse opinion of Roberts after being shown the ad, even after they were told it was false.
Over half (56 percent) of Democratic subjects disapproved of Roberts before the misinformation. That rose to 80 percent afterward, but even after correcting the misinformation, 72 percent of Democratic subjects still had a negative opinion. Republican volunteers, on the other hand, only showed a small increase in disapproval after watching the misinformation (11 percent vs 14 percent).
Correcting wrong info reinforces false beliefs Read More »
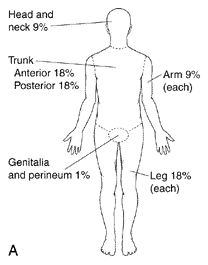 In the 1950s, doctors developed an easy way to estimate the ratio of the area of a patient’s burns to the total area of his skin. The system works by assigning standard percentages to major body parts. (Most of these happen to be multiples of nine.) The skin on each arm, for example, covers 9 percent of a patient’s total surface area. Each leg comprises 18 percent, as do the front and back of the torso. The head and neck together make up another 9 percent, and the last bit (or 1 percent) covers the genitalia and perineum. This breakdown makes it easy for doctors to estimate the size of a burn in relation to a body—a burn that covered half the arm would add 4 or 5 percent to the total figure. …
In the 1950s, doctors developed an easy way to estimate the ratio of the area of a patient’s burns to the total area of his skin. The system works by assigning standard percentages to major body parts. (Most of these happen to be multiples of nine.) The skin on each arm, for example, covers 9 percent of a patient’s total surface area. Each leg comprises 18 percent, as do the front and back of the torso. The head and neck together make up another 9 percent, and the last bit (or 1 percent) covers the genitalia and perineum. This breakdown makes it easy for doctors to estimate the size of a burn in relation to a body—a burn that covered half the arm would add 4 or 5 percent to the total figure. …