An analysis of botnets
From The Honeynet Project & Research Alliance’s “Know your Enemy: Tracking Botnets” (13 March 2005):
A botnet is a network of compromised machines that can be remotely controlled by an attacker. … With the help of honeynets we can observe the people who run botnets … Due to the wealth of data logged, it is possible to reconstruct the actions of attackers, the tools they use, and study them in detail. …
We have identified many different versions of IRC-based bots … The bot joins a specific IRC channel on an IRC server and waits there for further commands. This allows an attacker to remotely control this bot and use it for fun and also for profit. Attackers even go a step further and bring different bots together. Such a structure, consisting of many compromised machines which can be managed from an IRC channel, is called a botnet. IRC is not the best solution since the communication between bots and their controllers is rather bloated, a simpler communication protocol would suffice. But IRC offers several advantages: IRC Servers are freely available and are easy to set up, and many attackers have years of IRC communication experience.
… Even a relatively small botnet with only 1000 bots can cause a great deal of damage. These 1000 bots have a combined bandwidth (1000 home PCs with an average upstream of 128KBit/s can offer more than 100MBit/s) that is probably higher than the Internet connection of most corporate systems. In addition, the IP distribution of the bots makes ingress filter construction, maintenance, and deployment difficult. In addition, incident response is hampered by the large number of separate organizations involved. Another use for botnets is stealing sensitive information or identity theft: Searching some thousands home PCs for password.txt, or sniffing their traffic, can be effective.
The spreading mechanisms used by bots is a leading cause for “background noise” on the Internet, especially on TCP ports 445 and 135. … These malware scan large network ranges for new vulnerable computers and infect them, thus acting similar to a worm or virus. … most traffic targets the ports used for resource sharing on machines running all versions of Microsoft’s Windows operating system …
The traffic on these four ports [445/TCP, 139/TCP, 137/UDP, 135/TCP] cause more then 80 percent of the whole traffic captured. …
Lessons Learned
- Number of botnets
… able to track little more than 100 botnets during the last four months. … at the moment we are tracking about 35 active botnets.
- Number of hosts
During these few months, we saw 226,585 unique IP addresses joining at least one of the channels we monitored. … If an IRCd is modified not to show joining clients in a channel, we don’t see IPs here. Furthermore some IRCds obfuscate the joining clients IP address and obfuscated IP addresses do not count as seen, too. … this would mean that more then one million hosts are compromised and can be controlled by malicious attackers.
- Typical size of Botnets
Some botnets consist of only a few hundred bots. In contrast to this, we have also monitored several large botnets with up to 50.000 hosts. … botnets with over several hundred thousands hosts have been reported in the past. … We know about a home computer which got infected by 16 (sic!) different bots, so its hard to make an estimation about world bot population here.
- Dimension of DDoS-attacks
From the beginning of November 2004 until the end of January 2005, we were able to observe 226 DDoS-attacks against 99 unique targets.
- Spreading of botnets
“.advscan lsass 150 5 0 -r -s” and other commands are the most frequent observed messages. Through this and similar commands, bots spread and search for vulnerable systems.
- Harvesting of information
… harvesting of information from all compromised machines. With the help of a command like “.getcdkeys” the operator of the botnet is able to request a list of CD-keys (e.g. for Windows or games) from all bots.
- “Updates” within botnets
… observed updates of botnets quite frequently. … bots are instructed to download a piece of software from the Internet and then execute it. … bots can be dynamically updated and be further enhanced. … In total, we have collected 329 binaries. … Most of the other binary files are either adware …, proxy servers … or Browser Helper Objects.
An analysis of botnets Read More »
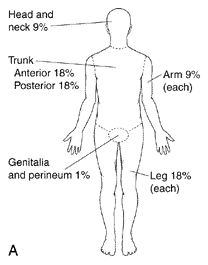 In the 1950s, doctors developed an easy way to estimate the ratio of the area of a patient’s burns to the total area of his skin. The system works by assigning standard percentages to major body parts. (Most of these happen to be multiples of nine.) The skin on each arm, for example, covers 9 percent of a patient’s total surface area. Each leg comprises 18 percent, as do the front and back of the torso. The head and neck together make up another 9 percent, and the last bit (or 1 percent) covers the genitalia and perineum. This breakdown makes it easy for doctors to estimate the size of a burn in relation to a body—a burn that covered half the arm would add 4 or 5 percent to the total figure. …
In the 1950s, doctors developed an easy way to estimate the ratio of the area of a patient’s burns to the total area of his skin. The system works by assigning standard percentages to major body parts. (Most of these happen to be multiples of nine.) The skin on each arm, for example, covers 9 percent of a patient’s total surface area. Each leg comprises 18 percent, as do the front and back of the torso. The head and neck together make up another 9 percent, and the last bit (or 1 percent) covers the genitalia and perineum. This breakdown makes it easy for doctors to estimate the size of a burn in relation to a body—a burn that covered half the arm would add 4 or 5 percent to the total figure. …