Buying startups also solves another problem afflicting big companies: they can’t do product development. Big companies are good at extracting the value from existing products, but bad at creating new ones.
Why? It’s worth studying this phenomenon in detail, because this is the raison d’etre of startups.
To start with, most big companies have some kind of turf to protect, and this tends to warp their development decisions. For example, Web-based applications are hot now, but within Microsoft there must be a lot of ambivalence about them, because the very idea of Web-based software threatens the desktop. So any Web-based application that Microsoft ends up with, will probably, like Hotmail, be something developed outside the company.
Another reason big companies are bad at developing new products is that the kind of people who do that tend not to have much power in big companies (unless they happen to be the CEO). Disruptive technologies are developed by disruptive people. And they either don’t work for the big company, or have been outmaneuvered by yes-men and have comparatively little influence.
Big companies also lose because they usually only build one of each thing. When you only have one Web browser, you can’t do anything really risky with it. If ten different startups design ten different Web browsers and you take the best, you’ll probably get something better.
The more general version of this problem is that there are too many new ideas for companies to explore them all. There might be 500 startups right now who think they’re making something Microsoft might buy. Even Microsoft probably couldn’t manage 500 development projects in-house.
Big companies also don’t pay people the right way. People developing a new product at a big company get paid roughly the same whether it succeeds or fails. People at a startup expect to get rich if the product succeeds, and get nothing if it fails. So naturally the people at the startup work a lot harder.
The mere bigness of big companies is an obstacle. In startups, developers are often forced to talk directly to users, whether they want to or not, because there is no one else to do sales and support. It’s painful doing sales, but you learn much more from trying to sell people something than reading what they said in focus groups.
And then of course, big companies are bad at product development because they’re bad at everything. Everything happens slower in big companies than small ones, and product development is something that has to happen fast, because you have to go through a lot of iterations to get something good.
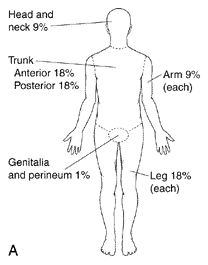 In the 1950s, doctors developed an easy way to estimate the ratio of the area of a patient’s burns to the total area of his skin. The system works by assigning standard percentages to major body parts. (Most of these happen to be multiples of nine.) The skin on each arm, for example, covers 9 percent of a patient’s total surface area. Each leg comprises 18 percent, as do the front and back of the torso. The head and neck together make up another 9 percent, and the last bit (or 1 percent) covers the genitalia and perineum. This breakdown makes it easy for doctors to estimate the size of a burn in relation to a body—a burn that covered half the arm would add 4 or 5 percent to the total figure. …
In the 1950s, doctors developed an easy way to estimate the ratio of the area of a patient’s burns to the total area of his skin. The system works by assigning standard percentages to major body parts. (Most of these happen to be multiples of nine.) The skin on each arm, for example, covers 9 percent of a patient’s total surface area. Each leg comprises 18 percent, as do the front and back of the torso. The head and neck together make up another 9 percent, and the last bit (or 1 percent) covers the genitalia and perineum. This breakdown makes it easy for doctors to estimate the size of a burn in relation to a body—a burn that covered half the arm would add 4 or 5 percent to the total figure. …