The Piraha language of Brazil
From Wikipedia’s “Pirahã language“:
The Pirahã language is a language spoken by the Pirahã – an indigenous people of Amazonas, Brazil, who live along the Maici river, a tributary of the Amazon.
Pirahã is believed to be the only surviving member of the Mura language family, all other members having become extinct in the last few centuries. It is therefore a language isolate, without any known connection to other languages. Despite having only ~150 speakers as of 2004, in eight villages along the Maici, it is not itself in immediate danger of extinction, as language use is vigorous and the Pirahã community is monolingual. …
Unusual features of Pirahã include:
- One of the smallest phoneme inventories of any known language [13]…, and a correspondingly high degree of allophonic variation, including two very rare sounds …
- The pronunciation of several phonemes depends on the speaker’s sex.
- An extremely limited clause structure.
- No grammatical numerals, not even “one” or “two”; the closest the language comes to numerals are general quantity words like [“a few”, “some”, and “many”].
- No abstract color words other than terms for light and dark.
- Few specific kin terms; one word covers both “father” and “mother” [and they appear not to keep track of relationships any more distant than biological siblings.]
- The entire set of personal pronouns appears to have been borrowed from Nheengatu, the Tupi-based lingua franca. Although there is no documentation of a prior stage of Pirahã, the close resemblance of the Pirahã pronouns to those of Nheengatu makes any other hypothesis improbable.
- Pirahã can be whistled, hummed, or encoded in music.
The occurrence of so many unusual linguistic features in a single language is remarkable.
The Piraha language of Brazil Read More »
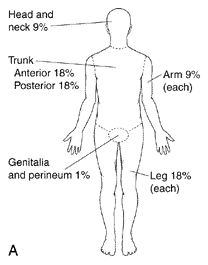 In the 1950s, doctors developed an easy way to estimate the ratio of the area of a patient’s burns to the total area of his skin. The system works by assigning standard percentages to major body parts. (Most of these happen to be multiples of nine.) The skin on each arm, for example, covers 9 percent of a patient’s total surface area. Each leg comprises 18 percent, as do the front and back of the torso. The head and neck together make up another 9 percent, and the last bit (or 1 percent) covers the genitalia and perineum. This breakdown makes it easy for doctors to estimate the size of a burn in relation to a body—a burn that covered half the arm would add 4 or 5 percent to the total figure. …
In the 1950s, doctors developed an easy way to estimate the ratio of the area of a patient’s burns to the total area of his skin. The system works by assigning standard percentages to major body parts. (Most of these happen to be multiples of nine.) The skin on each arm, for example, covers 9 percent of a patient’s total surface area. Each leg comprises 18 percent, as do the front and back of the torso. The head and neck together make up another 9 percent, and the last bit (or 1 percent) covers the genitalia and perineum. This breakdown makes it easy for doctors to estimate the size of a burn in relation to a body—a burn that covered half the arm would add 4 or 5 percent to the total figure. …